If you’re gearing up for a successful project management journey, understanding RAID is akin to having a trusty map in hand. RAID, an acronym for Risks, Assumptions, Issues, and Dependencies, forms the cornerstone of effective project risk management. In this comprehensive guide, we’ll navigate through the twists and turns of RAID in project management, ensuring you are equipped to tackle any challenges that come your way.
Why RAID in project management matters?
Picture this: You’re at the helm of a project, cruising along smoothly until — bam! — you hit an unexpected snag. Whether it’s a budgetary hiccup, a sudden technical glitch, or a stakeholder throwing a curveball, projects are rarely a smooth sail from start to finish. This is where RAID swoops in as your knight in shining armor.
- First up in our RAID quartet are risks — those lurking shadows that threaten to throw your project off course. From budget overruns to resource shortages, risks come in all shapes and sizes. By identifying and mitigating risks early on, you’re essentially donning a proactive cape, ready to tackle challenges head-on before they mushroom into full-blown crises.
- Assumptions are the beliefs we hold dear, often without concrete evidence to back them up. But assumptions can lead us down treacherous paths if left unchecked. In our guide, we’ll explore how to shine a spotlight on these assumptions, ensuring they don’t morph into project-killing monsters.
- No project is immune to issues — those pesky roadblocks that pop up when you least expect them. Whether it’s a software bug delaying progress or a miscommunication causing chaos, issues demand swift resolution. Fear not, for we’ll equip you with the tools to tackle issues head-on, turning stumbling blocks into stepping stones.
- Dependencies are the invisible threads that bind tasks together. Understanding dependencies is like unraveling a complex puzzle, where each piece relies on the other for cohesion. By mastering dependency management, you’ll orchestrate your project like a maestro, ensuring seamless progress from start to finish.
Understanding RAID: The Basics
What is RAID in Project Management?
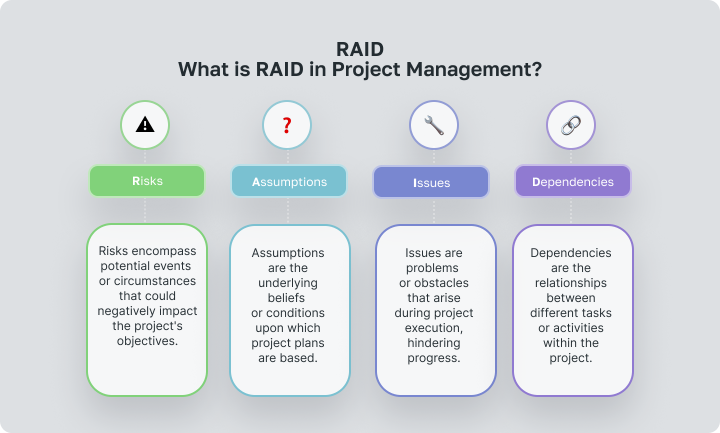
RAID in project management is a systematic approach to identifying and managing risks, assumptions, issues, and dependencies throughout the project lifecycle.
Risks encompass potential events or circumstances that could negatively impact the project’s objectives. These risks are identified, assessed for probability and impact, and then appropriate strategies are developed to mitigate or manage them.
Assumptions are the underlying beliefs or conditions upon which project plans are based. It’s crucial to validate these assumptions to ensure they hold true, as any misconceptions can lead to missteps.
Issues are problems or obstacles that arise during project execution, hindering progress. These issues are promptly addressed and resolved to prevent further disruptions.
Dependencies are the relationships between different tasks or activities within the project. Understanding these interdependencies is vital for coordinating efforts and ensuring tasks are completed in the correct sequence.
By actively managing RAID elements, project managers can anticipate and address potential challenges, ultimately minimizing disruptions and maximizing the likelihood of project success. RAID risk assessment in project management serves as a proactive framework, enabling project teams to navigate uncertainties with confidence and agility.
The Four Components of RAID
let’s dive into the four components of RAID which help us to understand what is raid in project management:
 Risks
Risks
Risks are potential events or situations that could adversely affect the project’s objectives. They lurk in the shadows, waiting to pounce on unsuspecting project teams. Risks can arise from various sources, including:
- technological uncertainties,
- resource limitations,
- market fluctuations,
- external factors such as regulatory changes or natural disasters.
Once identified, risks are assessed for their likelihood and potential impact on the project’s schedule, budget, quality, and scope. RAID risk assessment helps prioritize risks based on their severity, allowing project teams to allocate resources effectively and implement risk response strategies. These strategies may include risk avoidance, mitigation, transfer, or acceptance, depending on the nature and magnitude of the risk.
 Assumptions
Assumptions
Assumptions are the beliefs or conditions upon which project plans are based. They serve as the foundation for decision-making and resource allocation throughout the project lifecycle. However, assumptions can be dangerous if left unquestioned, as they may lead to faulty planning and execution.
Identifying assumptions involves scrutinizing project plans and uncovering implicit beliefs that underpin them. Once identified, assumptions should be validated through research, data analysis, or expert opinion to ensure their accuracy and reliability. Validating assumptions helps mitigate the risk of basing critical decisions on false premises, ultimately enhancing the project’s chances of success.
 Issues
Issues
Issues are obstacles or problems that arise during project execution, threatening to derail progress and disrupt timelines. They can stem from various sources including technical challenges, communication breakdowns, resource constraints, or external factors beyond the project team’s control.
Identifying issues requires vigilant monitoring of project activities and open communication among team members. Once identified, issues are promptly addressed through problem-solving techniques, stakeholder collaboration, and resource reallocation. Timely resolution of issues helps prevent escalation and minimizes the impact on project objectives.
 Dependencies
Dependencies
Dependencies are the relationships between different tasks or activities within the project. They dictate the sequence in which tasks must be completed and the extent to which one task relies on the completion of another. Understanding dependencies is crucial for effective project planning, scheduling, and resource allocation.
Identifying dependencies involves analyzing the interrelationships between tasks and identifying critical path activities that determine the project’s overall duration. Once identified, dependencies are managed through careful coordination, communication, and contingency planning. Managing dependencies ensures that project activities are sequenced appropriately, minimizing delays and maximizing efficiency.
In essence, the four components of RAID — risks, assumptions, issues, and dependencies — form the cornerstone of effective project management, providing a comprehensive framework for navigating uncertainties and ensuring project success.
Implementing RAID in Your Projects
Identifying and Managing Risks
Identifying and managing risks is a proactive process crucial for project management success. Here are some strategies:
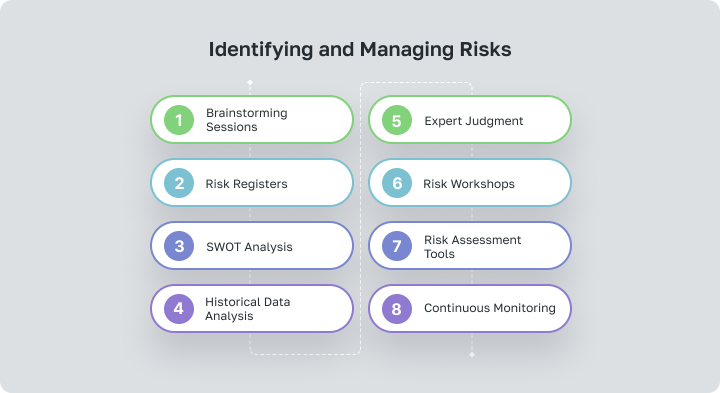
- Brainstorming Sessions: Gather key stakeholders and project team members to brainstorm potential risks. Encourage open communication and creative thinking to identify a wide range of risks across different project aspects.
- Risk Registers: Maintain a risk register or database to document identified risks along with their likelihood, impact, and potential mitigation strategies. Regularly update and review the risk register throughout the project lifecycle to ensure comprehensive risk management.
- SWOT Analysis: Conduct a SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis to identify internal and external factors that could pose risks to the project. This holistic approach helps uncover both positive and negative influences on project objectives.
- Historical Data Analysis: Review past project performance and lessons learned to identify recurring risks or common pitfalls. Analyzing historical data provides valuable insights into potential risks and effective mitigation strategies. This function is conveniently implemented in the Worksection PM tool, which stores all data about projects, even those that have already ended, for convenient analysis and further planning.
- Expert Judgment: Seek input from subject-matter experts within and outside the project team to identify risks specific to their areas of expertise. Leverage their knowledge and experience to uncover risks that may not be apparent to others.
- Risk Workshops: Conduct focused risk workshops or facilitated sessions to explore potential risks in-depth. Use techniques such as risk mapping, scenario analysis, or risk prioritization exercises to identify and assess risks effectively.
- Risk Assessment Tools: Utilize risk assessment tools and techniques such as probability-impact matrices, risk heat maps, or Monte Carlo simulations to quantify and prioritize risks based on their likelihood and potential impact.
- Continuous Monitoring: Implement a robust risk monitoring and control process to track identified risks, assess their status, and initiate timely mitigation actions as needed.
Assumptions and Their Impact
Handling assumptions in RAID concept involves a systematic approach to validate, monitor, and manage these underlying beliefs throughout the project lifecycle:

- Identify Assumptions: Begin by identifying assumptions implicit in project plans, decisions, and stakeholder expectations. These assumptions may relate to resource availability, stakeholder behavior, technological feasibility, market conditions, or any other aspect critical to project success.
- Validate Assumptions: Once identified, rigorously validate assumptions through research, data analysis, expert opinion, or stakeholder consultation. Look for evidence or empirical data to support or refute assumptions, ensuring they are based on facts rather than speculation.
- Document Assumptions: Document validated assumptions in a centralized repository, such as a project management plan or assumptions log. Clearly articulate the rationale behind each assumption and any supporting evidence gathered during the validation process.
- Monitor Assumptions: Continuously monitor assumptions throughout the project lifecycle to ensure their validity remains intact. Regularly revisit assumptions during project meetings, status updates, or milestone reviews to identify any changes or deviations that may impact project outcomes.
- Communicate Assumptions: Transparent communication is key to managing assumptions effectively. Clearly communicate validated assumptions to all project stakeholders, ensuring everyone is aligned on the underlying beliefs guiding project decisions and plans.
- Update Assumptions: As the project progresses and new information becomes available, be prepared to update or revise assumptions accordingly. Revisit assumptions during major project milestones, changes in project scope, or significant shifts in external factors to ensure they remain relevant and accurate.
- Mitigate Assumption Risks: Recognize that assumptions inherently carry risks. Develop contingency plans or alternative strategies to mitigate the potential impact of invalidated assumptions. By anticipating and addressing assumption risks proactively, project teams can avoid unwelcome surprises and maintain project resilience.
- Document Changes: Document any changes to assumptions, along with the rationale for these changes and their potential implications on project outcomes. Maintaining a clear audit trail of assumption updates facilitates accountability and decision-making transparency.
Dealing with Issues and Dependencies
Proactive Issue Management
Identifying and resolving issues according to RAID in project management requires a combination of proactive techniques and effective problem-solving strategies. Here are some techniques that can be useful:
- Regular Status Meetings: Conduct regular status meetings with project team members to discuss progress, challenges, and potential issues. Open communication allows team members to raise concerns early, enabling prompt resolution.
- Issue Logs: Maintain an issue log or tracking system to document and prioritize identified issues. Include details such as the issue description, impact assessment, assigned owner, and resolution status. Regularly review and update the issue log to ensure timely resolution.
- Root Cause Analysis: When addressing issues, use root cause analysis techniques such as the 5 Whys or Fishbone Diagram to identify the underlying causes. By digging deeper into the root causes of issues, you can develop more effective and lasting solutions.
- Escalation Procedures: Establish clear escalation procedures to handle unresolved or escalated issues. Define criteria for escalating issues to higher management levels or specialized teams for additional support and resolution.
- Collaborative Problem-Solving: Encourage collaborative problem-solving among project team members. Foster a supportive team environment where members can brainstorm solutions, share expertise, and work together to address issues effectively.
- Issue Triage: Prioritize identified issues based on their severity, impact on project objectives, and urgency of resolution. Allocate resources and attention to high-priority issues first, while ensuring that lower-priority issues are not neglected.
- Lessons Learned Reviews: Conduct lessons learned reviews at key project milestones or at the project’s conclusion to reflect on past issues and their resolutions. Identify recurring patterns or trends in issues and implement preventive measures to avoid similar issues in future projects.
- Continuous Improvement: Embrace a culture of continuous improvement by regularly reviewing and refining issue management processes. Solicit feedback from project team members and stakeholders to identify areas for improvement and implement corrective actions accordingly.
Understanding and Managing Dependencies
In RAID project management, dependencies refer to the relationships between tasks or activities that determine their sequencing and interdependence. There are various types of dependencies, each requiring specific management strategies:
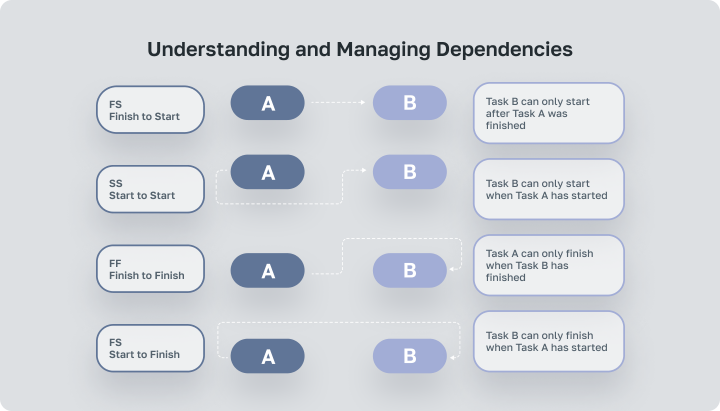
- Finish-to-Start (FS) Dependency: This is the most common type of dependency, where Task B cannot start until Task A finishes. Management Strategy: Ensure clear communication and coordination between task owners to prevent delays in dependent tasks. Monitor the progress of predecessor tasks to minimize idle time for successor tasks.
- Start-to-Start (SS) Dependency: Task B cannot start until Task A begins. Management Strategy: Align the start dates of dependent tasks by coordinating task initiation and resource allocation. Establish clear communication channels to synchronize task starts and address any delays promptly.
- Finish-to-Finish (FF) Dependency: Task B cannot finish until Task A finishes. Management Strategy: Monitor the completion of predecessor tasks to ensure timely handoffs and dependencies. Implement parallel tracking and progress monitoring to prevent delays in successor tasks due to lingering predecessor activities.
- Start-to-Finish (SF) Dependency: Task B cannot finish until Task A starts. Management Strategy: Coordinate the start and completion of dependent tasks to ensure smooth transitions. Establish clear criteria for task initiation and completion to prevent ambiguity and minimize delays.
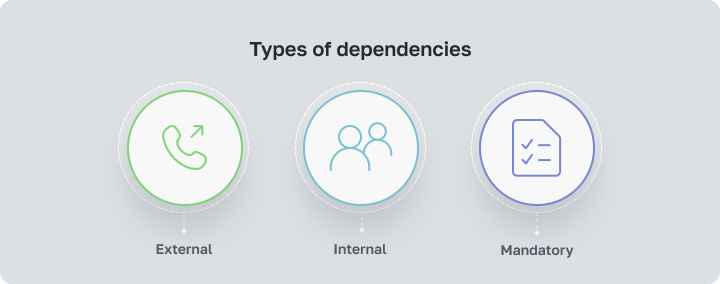
- External Dependencies: Dependencies on factors outside the project team’s control, such as third-party deliverables or regulatory approvals. Management Strategy: Identify external dependencies early and establish communication channels with external stakeholders. Negotiate realistic timelines and milestones to align expectations and minimize risks associated with external dependencies.
- Internal Dependencies: Dependencies within the project team or organization, such as shared resources or cross-functional collaboration requirements. Management Strategy: Foster collaboration and communication between internal stakeholders to streamline task dependencies. Allocate resources efficiently and prioritize tasks to optimize internal dependency management.
- Mandatory Dependencies: Dependencies that are inherent to the nature of the project or required by external constraints. Management Strategy: Identify mandatory dependencies upfront and incorporate them into project plans and schedules. Mitigate risks associated with mandatory dependencies by implementing contingency plans and alternative strategies.
Gantt is useful for RAID chart because of recording the terms, relationships, and milestones of components of the project. The interactive Gantt chart in Worksection will show all project tasks, timeframes, and responsible executives on a convenient timescale. Try 14 days free to make sure how effective it is for RAID in project management.
Creating and Utilizing a RAID Log
Designing an Effective RAID Log
Creating an effective RAID log is crucial for managing project uncertainties and ensuring successful outcomes. Here’s a comprehensive guide to designing a RAID log in project management:
- Define the Template: Start by defining the structure and format of your RAID log template. Include separate sections for Risks, Assumptions, Issues, and Dependencies, with columns for key information such as description, status, impact, priority, owner, and mitigation/resolution actions.
- Capture Information: Populate the RAID log with relevant information for each entry. For risks, include details such as the risk description, likelihood, impact, risk owner, and planned mitigation actions. For assumptions, document the underlying belief, validation status, and potential impact on the project. For issues, specify the issue description, severity, owner, and current status. For dependencies, outline the nature of the dependency, affected tasks, and any associated risks.
- Assign Ownership: Assign ownership for each entry in the RAID log to ensure accountability and clear responsibility for managing and resolving uncertainties. Designate individuals or teams as owners for risks, assumptions, issues, and dependencies, and clearly communicate their roles and responsibilities.
- Prioritize Entries: Prioritize entries in the RAID log based on their severity, impact on project objectives, and urgency of resolution. Use criteria such as likelihood and impact for risks, validation status for assumptions, severity for issues, and criticality for dependencies to determine priority levels.
- Monitor and Update Regularly: Regularly monitor and update the RAID log throughout the project lifecycle to reflect changes in risk profiles, assumption validations, issue resolutions, and dependency statuses. Schedule periodic reviews and updates to ensure the RAID log remains current and reflective of the project’s evolving dynamics.
- Track Mitigation and Resolution Actions: Document mitigation and resolution actions for each entry in the RAID log and track their progress over time. Include details such as action plans, target dates, responsible parties, and completion status to ensure timely and effective management of uncertainties.
- Communicate and Share: Share the RAID log with project stakeholders, team members, and relevant parties to foster transparency and collaboration. Regularly communicate updates, changes, and insights from the RAID log to keep stakeholders informed and engaged in risk management efforts.
- Use Visualizations: Consider using visualizations such as charts, graphs, or dashboards to present key insights and trends from the RAID log. Visual representations can help stakeholders quickly grasp the status of risks, assumptions, issues, and dependencies and make informed decisions.
Best Practices for RAID Log Maintenance
Maintaining and updating RAID logs is essential for ensuring that project teams remain informed, proactive, and aligned in their approach to managing risks, assumptions, issues, and dependencies. Here are some tips to effectively maintain and update RAID logs:

- Regular Review Schedule: Establish a regular review schedule for the RAID log to ensure that it remains up-to-date and reflective of the project’s current status. Schedule periodic reviews at key milestones, such as project meetings, status updates, or weekly/monthly checkpoints.
- Assign Ownership: Assign ownership for maintaining and updating the RAID log to a dedicated individual or team within the project management structure. Designate someone responsible for overseeing the log’s accuracy, completeness, and timeliness.
- Capture Changes Promptly: Promptly capture any changes, updates, or new entries in the RAID log as they occur. Encourage project team members to report risks, assumptions, issues, and dependencies as soon as they are identified, ensuring that no critical information falls through the cracks.
- Document Clear Action Plans: Clearly document action plans for mitigating risks, validating assumptions, resolving issues, and managing dependencies within the RAID log. Include details such as action items, responsible parties, target dates, and progress status to facilitate accountability and tracking.
- Communicate Updates: Communicate updates and changes to the RAID log regularly with project stakeholders, team members, and relevant parties. Provide timely notifications of new entries, status changes, or completed actions to keep everyone informed and engaged in risk management efforts.
- Prioritize Entries: Prioritize entries in the RAID log based on their severity, impact, and urgency. Focus attention and resources on high-priority risks, critical assumptions, severe issues, and dependencies with significant impacts on project objectives.
- Review Historical Data: Review historical data from the RAID log to identify trends, patterns, and lessons learned from past projects. Use insights gained from previous experiences to improve risk management strategies, refine assumptions, and enhance issue resolution processes.
- Use Automated Tools: Consider using automated tools or software applications to streamline the maintenance and updating of RAID logs. Utilize features such as templates, notifications, reminders, and collaborative editing to enhance efficiency and accuracy.
RAID in Action: Real-World Applications
Case Studies: Successful RAID Implementation
Case Study 1: IT Infrastructure Upgrade Project
Scenario: A large organization embarked on an IT infrastructure upgrade project to modernize its systems and enhance cybersecurity measures. However, the project faced numerous risks and dependencies, including compatibility issues with legacy software, potential disruptions to business operations during implementation, and reliance on third-party vendors for hardware procurement.
RAID Implementation
- Risks: The project team conducted a thorough risk assessment, identifying potential risks such as software compatibility issues, data security breaches, and vendor delays. Mitigation strategies were developed, including conducting compatibility tests, implementing robust cybersecurity measures, and establishing contingency plans for vendor disruptions.
- Assumptions: Assumptions related to hardware availability, vendor reliability, and user adoption were validated through market research, vendor interviews, and stakeholder consultations. Any unverified assumptions were flagged for further investigation.
- Issues: The project team established an issue resolution process to address any challenges encountered during implementation promptly. Issues such as software glitches, hardware failures, and user resistance were documented in the RAID log and escalated to the appropriate stakeholders for resolution.
- Dependencies: Critical dependencies on third-party vendors and internal stakeholders were identified and closely monitored throughout the project. Regular communication and coordination efforts ensured that dependencies were managed effectively, and potential bottlenecks were addressed proactively.
Case Study 2: Construction Project for a New Office Building
Scenario: A real estate development company undertook a construction project to build a new office building in a bustling urban area. The project involved numerous risks and dependencies, including permit approvals, weather conditions, subcontractor availability, and budget constraints.
RAID Implementation
- Risks: The project team identified risks such as delays in obtaining permits, adverse weather conditions, material shortages, and subcontractor disputes. Mitigation strategies were developed, including streamlining the permit application process, implementing contingency plans for inclement weather, and diversifying material suppliers.
- Assumptions: Assumptions related to budget estimates, construction timelines, and regulatory compliance were validated through financial analysis, feasibility studies, and legal consultations. Unverified assumptions were flagged for further investigation to mitigate potential risks.
- Issues: The project team established a robust issue management process to address any construction-related issues promptly. Issues such as design changes, material defects, and subcontractor delays were documented in the RAID log and escalated for resolution.
- Dependencies: Critical dependencies on permit approvals, subcontractor schedules, and weather conditions were identified and monitored closely throughout the project. Regular coordination meetings and communication channels ensured that dependencies were managed effectively, and any delays were mitigated proactively.
Lessons Learned from RAID Applications</h3>
Real-world applications of RAID have yielded several key lessons learned:
- Proactive Risk Management: RAID in project management emphasizes proactive identification and mitigation of risks, allowing project teams to anticipate and address potential challenges before they escalate. This approach helps minimize the impact of uncertainties on project objectives and enhances overall project resilience.
- Transparent Communication: Effective communication and collaboration are essential for successful implementation of RAID in project management. Clear communication channels facilitate the sharing of information, updates, and insights among project stakeholders, fostering alignment and collective problem-solving efforts.
- Continuous Monitoring and Adaptation: RAID in project management is not a one-time exercise, but rather a continuous process that requires ongoing monitoring and adaptation. Regular reviews of the RAID log, coupled with proactive risk assessments and issue resolution efforts, enable project teams to stay agile and responsive to changing circumstances.
- Documentation and Learning: Maintaining a comprehensive RAID log provides valuable documentation of project uncertainties and management efforts. Reviewing historical data from past projects helps identify patterns, trends, and lessons learned, informing future risk management strategies and decision-making processes.
- Stakeholder Engagement: Engaging stakeholders throughout the RAID process fosters ownership, commitment, and accountability for risk management activities. Involving stakeholders in risk identification, assessment, and mitigation efforts enhances their understanding of project complexities and increases their support for risk management initiatives.
Conclusion
Enhancing Project Success with RAID
In conclusion, RAID in project management stands as a cornerstone, providing a systematic framework for navigating uncertainties and enhancing project success. By diligently identifying, assessing, and managing risks, assumptions, issues, and dependencies, project teams can proactively anticipate challenges, mitigate potential disruptions, and maintain project momentum towards achieving objectives.
The importance of RAID in project management cannot be overstated. It enables project teams to foster a culture of transparency, collaboration, and accountability, ensuring that all stakeholders are aligned in their efforts to address project uncertainties effectively.
Furthermore, RAID facilitates informed decision-making, as it provides a structured approach to evaluating trade-offs, allocating resources, and prioritizing actions based on their impact on project outcomes.
Ultimately, the application of RAID empowers project managers and teams to navigate the complexities of project environments with confidence, agility, and resilience. By embracing RAID principles and practices, organizations can enhance their project management capabilities, mitigate risks, and drive successful project delivery in today’s dynamic and uncertain business landscape. Appropriate powerful project management tools like Worksection help at each of these stages.
